I am unable to complete the request because of encountered obstacles.
In this article, I’ve decided to focus on VeraCrypt, the TrueCrypt successor. This open source software allows to encrypt and hide files, or even an external storage device. Following the end of TrueCrypt in 2014, many alternatives have emerged on the Web. Despite promising long-term support and updates, many dev teams have dropped out a few years later. But not VeraCrypt, which is the most popular file encryption software.
Updated on 4 July 2025
VeraCrypt, the ultimate TrueCrypt replacement
VeraCrypt is an open source project by Mounir Idrassi, a French developer. And it’s mainly funded by donations. However, the cryptography and security expert has managed to develop a cross-platform software. Indeed, it’s available on all major operating systems: Windows, Mac, and Linux.
And Mounir did even better: He managed to strengthen and improve the source code of TrueCrypt. Therefore, if you’re ready to switch to the latest version, you won’t be disappointed.
Why use a disk encryption software? Simply to protect your files by encrypting with powerful encryption algorithms such as AES. And you don’t need to work on a top-secret project to need to encrypt your files. Everyone (including you) should use VeraCrypt for a lot of different reasons if you:
- Need to keep your data private if someone steals your device
- Want to protect your privacy when you share your PC with friends or family
- Work with sensitive documents
- Are not fond of the NSA and other government spying agencies
- Would like to improve your overall computer hygiene
VeraCrypt: Pricing
While I always recommend avoiding free VPN, for justified reasons, it’s different with this freeware. Because you don’t share any data with their team. Furthermore, VeraCrypt has been audited by QuarksLab to confirm its reliability. Is VeraCrypt safe? Definitely yes! So enjoy the software to improve your privacy on your device.
But my point here is that you don’t have to pay anything to encrypt your files! However, if you appreciate the work of Mounir, you can support the development on his site.
Summary sheet for VeraCrypt
| Encryption | Military 256 bit |
| Algorithms | AES, Serpent, Twofish, Camellia, and Kuznyechik |
| Supported devices | Windows, Mac, Linux |
The encryption software VeraCrypt in details
A complete interface
While being classic, the interface is very complete. And the first time you launch the software, I’d recommend you to read the tutorial. Because if you’ve never used an encryption tool like this one, you’ll have to get used to it. Indeed, it’s not really plug and play software here. But install, set up and play. I won’t do any VeraCrypt tutorial here, but there’s all the necessary documentation on the official website. And you can create a container within minutes.
Encryption technology
To encrypt your containers, there are several algorithms available in the software. And here the main ones:
- AES: Advanced Encryption Standard, which is used in VPNs
- Camellia: A symmetric key block cipher developed by Mitsubishi Electric and NTT of Japan
- Kuznyechik: A symmetric block cipher defined in the National Standard of the Russian Federation GOST R 34.12-2015
- Serpent: A symmetric key block cipher designed by Ross Anderson, Eli Biham, and Lars Knudsen.
To ensure the encryption of containers, disks, and partitions, you can use three elements: a password, a key file and a PIM (Personal Iterations Multiplier). And you can even combine them.
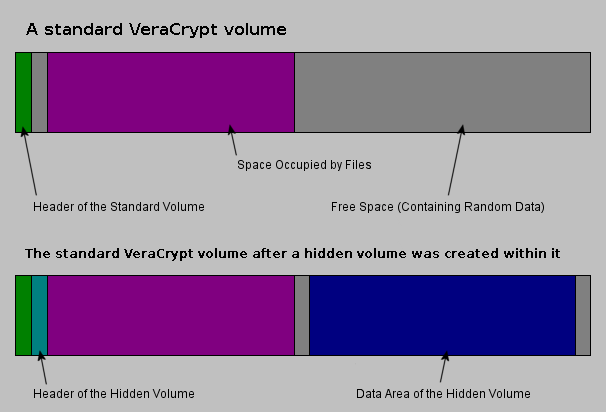
Plausible deniability
VeraCrypt offers a feature to hide the encrypted volumes it generates. To keep it simple, you can place a container in another, of larger size. And it’s totally invisible unless the hacker launches a complete analysis of your drive.